The Vulnerability Assessment Tool is also available in a version supporting interactive group sessions with stakeholders. This version is not available online but needs to be used on a local client (see Make Your Own).
Learn more about the tool “Vulnerablity Assessment (GROUPMODE)” here
Conceptual Approach
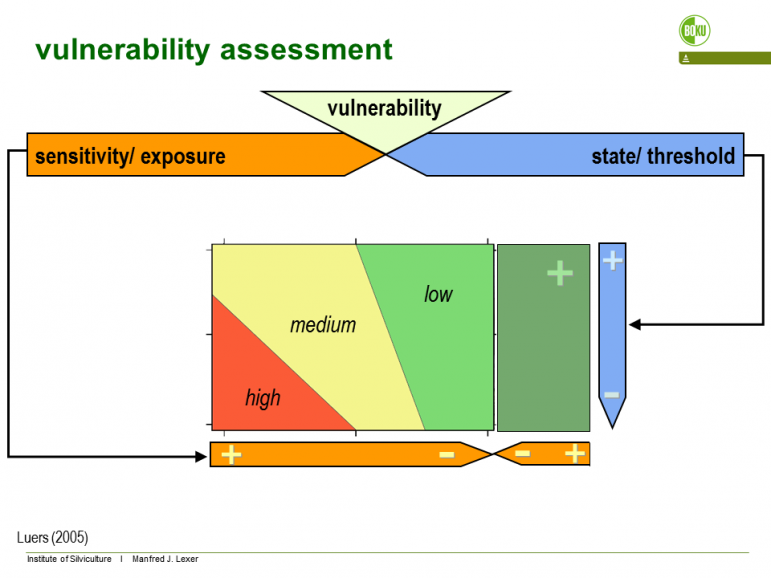
Figure 1. Conceptual representation of the vulnerability surface. The total perceived impact is aggregated from impacts on indicators that are available from forest ecosystem simulations. Values on the y-axis (adaptive capacity) are derived from user input.
The two-dimensional vulnerability surface can be collapsed to a one-dimensional sensitivity index and thus the need to provide user input on adaptive capacity is dropped. To evaluate the sensitivity indicators on a dimensionless scale [0-1] thresholds for recognition and tolerance of an impact must be defined for all indicators. In the manager variant these thresholds are fixed while the analyst variant of the Vulnerability Assessment Tool allows access to advanced features of the tool where thresholds and underlying preference functions which transfer the original measurement scale of the sensitivity indicators into a dimensionless index [0-1] can be adjusted according to specific stakeholder needs. Applying additive value functions from multi-criteria methodology the indicators can be aggregated at the level of ecosystem services, or across all involved services to yield an overall “multifunctional” vulnerability index. For details we refer to Seidl et al. (2011) and Lexer and Seidl (2009).
Literature
Seidl, R., Rammer, W., Lexer, M.J. 2011. Climate change vulnerability of sustainable forest management in the Eastern Alps.Climatic Change 106:225–254
Füssel, H.M., Klein, R.J.T. 2006. Climate change vulnerability assessments: an evolution of conceptual thinking. Clim Change 75:301–329
Usage hints and guides
The “group mode” requires special preparation (creation of group users, …) and is not supported by default.
If you are interested in this group mode component, please contact Manfred J. Lexer (mj.lexer@boku.ac.at) or Werner Rammer (werner.rammer@boku.ac.at).
Screenshots & Impressions
- A group session is led by a moderator team that provides also additional context information
- Users working with the tool in a group session
- The collected preferences within the group can be viewed interactively.